Log files are essential diagnostic tools that record detailed information about Gridinsoft Anti-Malware’s operations. These files help our support team troubleshoot issues and provide you with insights into the software’s performance. Understanding how to access and interpret these logs can improve your malware protection experience.
Types of Log Files
Gridinsoft Anti-Malware generates three distinct types of log files, each serving a specific purpose in monitoring different aspects of the software’s operation:
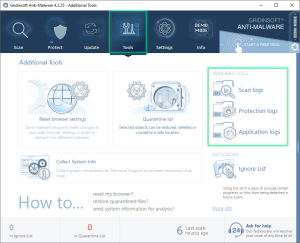
Scan Logs
Scan logs maintain comprehensive records of every scanning process, whether completed or interrupted. Each scan generates a separate log file containing detailed information about the scanning procedure, detected threats, and actions taken.
Protection Logs
Protection logs record activity from all three types of real-time protection when at least one protection module is enabled. These logs track real-time threat detection and blocking activities.
Application Logs
Application logs are crucial for diagnosing software behavior issues. These logs help identify errors, incorrect data processing, or other application-related problems that may affect performance.
Accessing and Managing Log Files
All log files are accessible through the Tools tab in the Gridinsoft Anti-Malware interface. You can filter and manage these logs based on your specific needs.
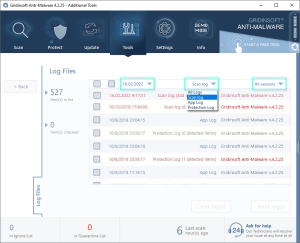
Filtering Options
The log management interface provides several filtering options to help you locate specific information:
- By Type: View scan logs, protection logs, or application logs separately
- By Date: Filter logs from specific time periods
- By Software Version: View logs from different program versions
- Combined View: Display all log types together with date or version filtering
Filtering Options
The log management interface provides several filtering options to help you locate specific information:
- By Type: View scan logs, protection logs, or application logs separately
- By Date: Filter logs from specific time periods
- By Software Version: View logs from different program versions
- Combined View: Display all log types together with date or version filtering
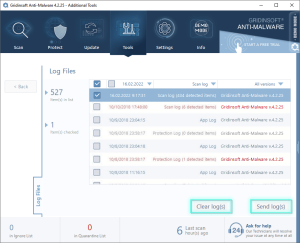
Sending Log Files to Support
When contacting our support team, providing relevant log files significantly helps with troubleshooting and issue resolution.
How to Send Logs
- Navigate to the Tools tab
- Select the appropriate log type (Scan Log, Protection Log, or Application Log)
- Check the boxes next to the specific logs you want to send
- Click the “Send log(s)” button to transmit them to our support team
Once you select at least one log file, the “Clear log(s)” and “Send log(s)” buttons become available for use.
Log File Storage Settings
You can configure how long log files remain stored on your computer through the Settings tab.
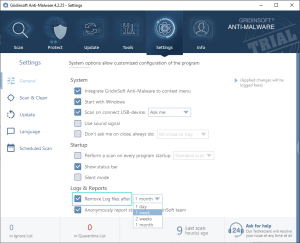
Storage Management:
If automatic log deletion is not enabled, log files will accumulate on your computer indefinitely. Enable automatic cleanup to maintain optimal disk space usage while retaining necessary diagnostic information.
These log files are invaluable when contacting our Support Center, as they provide detailed insights into settings, scan options, and system behavior during troubleshooting.
Understanding Removal Results
After completing a malware removal process, Gridinsoft Anti-Malware displays detailed results showing the status of each processed item.
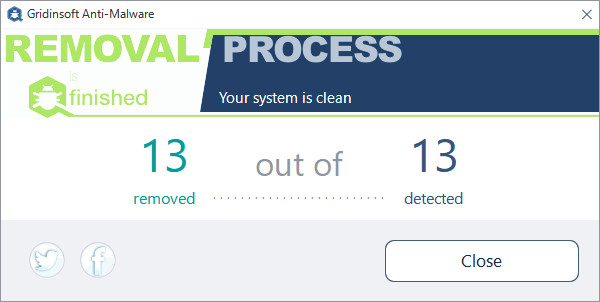
Result Indicators
The removal process uses specific symbols to indicate the status of each processed item:
|
|
Success (Arrow): Indicates an item that was successfully processed and removed from your system. |
|
|
Pending Removal (Cross): Marks files that couldn’t be removed immediately, typically because they’re currently in use. These items can usually be removed after a system restart. The program will prompt you to restart if necessary. |
Removal Process Timeline
The removal process typically takes from several seconds to a few minutes, depending on the size and number of files being removed. If any detected files cannot be removed, the program will provide detailed information about the issue.
Grouped Threats and Connected Items
Sometimes you’ll see connected items in the removal results. These represent grouped threats that consist of multiple components:
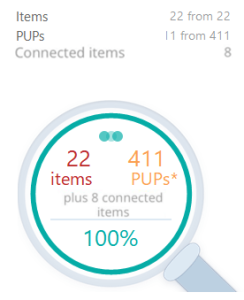
For example, a single threat might include:
![]()
- An executable file
- Multiple registry entries
- Associated configuration files
While these components are grouped as one threat during scanning, they’re processed individually during removal. This detailed reporting ensures you understand exactly what actions were taken on your system.
Troubleshooting and Support
If you experience issues with malware removal or need assistance interpreting log files, our support team is ready to help.
Getting Help:
- Contact our Support Team for removal assistance
- Include relevant log files when submitting support requests
- If a file was removed by mistake, check the Quarantine section in the Tools tab for restoration options
Our specialists will analyze your log files and provide personalized solutions to resolve any malware protection issues you encounter.
