The Protection tab provides a comprehensive overview of your system’s current security status and real-time protection capabilities. Gridinsoft Anti-Malware offers three powerful proactive protection modules that work together to safeguard your computer: Internet Security, On-Run Protection, and USB Protection. This centralized dashboard allows you to monitor, control, and review all protection activities from a single interface.
Protection Tab Overview
The Protection tab serves as your security command center, displaying essential information about your system’s defensive status:
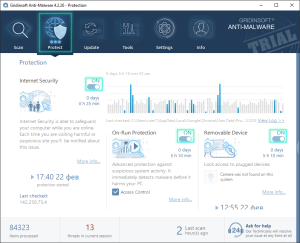
Key Information Available
The Protection tab displays the following critical security data:
- Current Protection Level: Overall security status based on the number of active protection modules
- Activity Duration: How long your protection modules have been running continuously
- Real-Time Report Log: Detailed records of detected threats and actions taken by each protection module
- Detection Statistics: Total count of scanned and detected objects, broken down by individual protection elements
Core Protection Modules
Gridinsoft Anti-Malware’s protection system consists of three specialized modules, each designed to address specific threat vectors:
Internet Security
Internet Security provides comprehensive web-based threat protection by monitoring and filtering your internet activity. This module:
- Blocks access to known malicious and suspicious websites
- Provides warnings before accessing potentially dangerous resources
- Scans web content for malicious scripts and harmful code
- Prevents drive-by downloads and browser-based attacks
When you attempt to visit a suspicious website or access content with malicious scripts, Internet Security will either display a warning message asking for confirmation or completely block access depending on the threat severity.
On-Run Protection
On-Run Protection acts as a real-time sentinel for your system, monitoring file execution and system activities. This module:
- Scans newly downloaded files before they can execute
- Monitors system processes for suspicious behavior
- Detects and blocks malware before it can cause damage
- Provides immediate threat response and quarantine capabilities
This proactive protection ensures that malicious software is identified and neutralized at the moment of execution, preventing system compromise.
USB Protection (Removable Device Protection)
USB Protection safeguards your system from threats that may arrive via removable storage devices. This module:
- Automatically scans USB drives, external hard drives, and other removable media
- Blocks execution of files on infected devices until scanning is complete
- Prevents autorun malware from launching automatically
- Provides detailed scan results before allowing device access
This protection is particularly important as infected USB drives and external storage devices are common vectors for malware distribution.
Layered Protection Approach:
These three protection modules work together to create multiple layers of defense. Internet Security protects during web browsing, On-Run Protection monitors file execution, and USB Protection secures removable media access. This comprehensive approach ensures threats are caught regardless of their entry point.
Accessing and Understanding Protection Logs
The protection log system provides detailed records of all security actions taken by Gridinsoft Anti-Malware. This information is crucial for understanding your system’s threat landscape and verifying protection effectiveness.
Viewing Protection Logs
To access detailed protection logs:
- Navigate to the Protection tab
- Locate the “View Log>>” button (displayed in blue text)
- Click the button to open the comprehensive log viewer
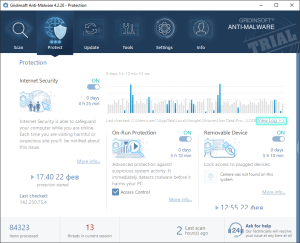
Log Information Details
Each log entry contains comprehensive information about protection activities:
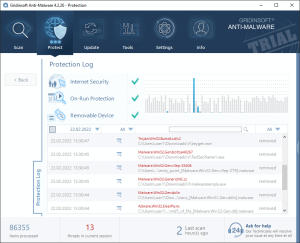
The log entries include:
- Date and Time: Precise timestamp of when each action occurred
- Protection Module: Which specific protection component detected the threat
- Object Details: Information about the detected file, URL, or system component
- Action Taken: What response was applied (blocked, quarantined, allowed, etc.)
- Threat Classification: Type and severity of the detected threat
Managing Protection Actions
The protection log system not only records security events but also allows you to modify or reverse certain actions when appropriate.
Reversible Actions
Many protection actions can be undone or modified through the log interface:
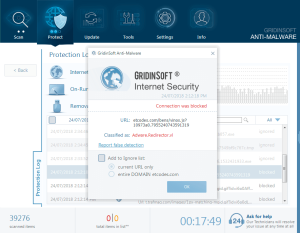
Available Action Modifications
From the protection logs, you can:
- Restore Quarantined Items: Recover files that were incorrectly identified as threats
- Add to Ignore List: Exclude trusted files or websites from future detection by adding them to your ignore list
- Unblock Websites: Remove web filtering restrictions for specific URLs
- Adjust Protection Settings: Modify detection sensitivity for specific protection modules
Important Considerations:
When modifying protection actions, ensure you understand the security implications. Only restore or ignore items that you are confident are legitimate and safe. When in doubt, consult the log details or contact support for guidance.
Optimizing Your Protection Configuration
To maintain optimal security while minimizing false positives:
- Regular Log Review: Periodically check protection logs to identify patterns and adjust settings
- Module Customization: Enable or disable specific protection modules based on your usage patterns
- Exception Management: Use the ignore list judiciously for trusted applications and websites
- Update Monitoring: Ensure protection modules stay current with the latest threat signatures
- Performance Balance: Adjust protection levels to balance security with system performance
Best Practices for Protection Management
To maximize the effectiveness of your protection system:
- Keep All Modules Active: Unless specific compatibility issues arise, maintain all three protection modules in active status
- Monitor Statistics: Regularly review detection counts and activity logs to understand your threat environment
- Prompt Response: Address protection alerts promptly rather than dismissing them
- Regular Maintenance: Periodically clear old log entries and review ignore list contents
- Documentation: Keep notes about any protection modifications for future reference
The Protection tab serves as your central hub for monitoring and managing Gridinsoft Anti-Malware’s real-time security capabilities. By understanding and effectively utilizing these protection features, you can maintain robust security while ensuring smooth system operation.
